Checkpoint and Cisco site-to-site VPN
This guide shows you how to create site-to-site VPN tunnel between checkpoint firewall and cisco router. Let's begin:
Checkpoint
IP address: 1.1.1.2
Network behind: 172.20.200.0/24
Create a network object that is the network that will be sitting behind the new Cisco router

Set the NAT – for Internet routing

Create a network object that is the network that will be sitting behind Checkpoint firewall:

Set the NAT – for Internet routing

Create a new interoperable device on CheckPoint for Cisco router

On Topology option, add external Interface

Note picture above is wrong (should be 1.1.1.1) – sorry$
Mark it as an external interface

Create an internal Interface:

Mark it as an Internal interface which leads to the network behind Cisco router

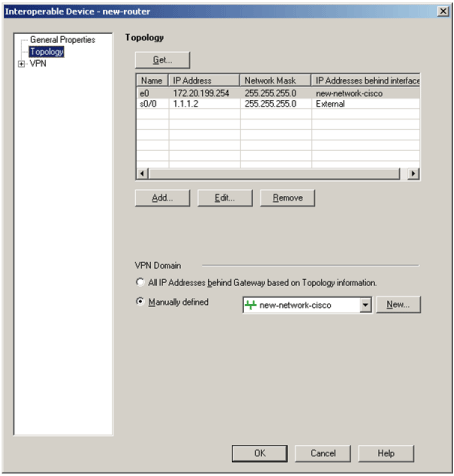
On the VPN domain option, choose manually defined: and assign the network that is behind Cisco router
On the VPN Manager, create a new community or join the new interoperable device to the existing community (either meshed or star)
Create a new one:

On the participating gateway, put the Cisco router and Checkpoint firewall

On the VPN properties, make sure the phase 1 and phase 2 is having the same setup in both Cisco (later) and Checkpoint
In this example we are using 3des-md5 for phase 1 and aes-128-md5 for phase 2

On the Advanced Properties, make sure the phase 1 and phase 2 is having the same setup in both Cisco (later) and Checkpoint
In this example we are using group 2 for phase 1 diffie-hellman group
Disable NAT inside VPN community – so that site-to-site VPN is not Natted

On Shared Secret page, put the share secret on to be used with Cisco router:

Create a rule in Checkpoint firewall to encrypt the traffic between network behind each firewall:

Push the policy to the CheckPoint firewall!
Cisco
IP address: 1.1.1.1
Network behind: 172.20.199.0/24
Create the isamkmp policy:
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
Create the crypto key:
crypto isakmp keyaddress 1.1.1.2 no-xauth
where shared-key is the shared key you setup in Checkpoint and 1.1.1.2 is the checkpoint IP address
Create transform set:
crypto ipsec transform-set cm-transformset-1 esp-aes esp-md5-hmac
Create the crypto-map:
crypto map cm-cryptomap 1 ipsec-isakmp
description VPN tunnel to Checkpoint
set peer 1.1.1.2
set security-association lifetime seconds 28800
set transform-set cm-transformset-1
match address 111
Create the outbound access list inside VPN (allow Cisco network to Checkpoint network):
access-list 111 permit ip 172.20.199.0 0.0.0.255 172.20.200.0 0.0.7.255
Create the inbound access list for external interface:
access-list 101 permit icmp any any
access-list 101 permit ip 1.1.1.2 0.0.0.0 any
access-list 101 permit ip 172.20.200.0 0.0.0.255 any
access-list 101 deny ip any any log
Assign crypto-map to the external interface:
interface Serial0/0
bandwidth 2048
ip address 1.1.1.1 255.255.255.0
ip access-group 101 in
no ip proxy-arp
ip nat outside
ip route-cache flow
no cdp enable
crypto map cm-cryptomap
Configure internal interface:
interface FastEthernet0/0
description Cisco LAN
ip address 172.20.199.254 255.255.255.0
no ip proxy-arp
ip nat inside
ip route-cache flow
speed 100
full-duplex
ntp broadcast
no cdp enable
Create the NAT rule:
ip nat inside source route-map nonat interface Serial0/0 overload
route-map nonat permit 10
match ip address 150
Create access list for NAT:
Do-not NAT traffic between sites
NAT everything else
access-list 150 deny ip 172.20.199.0 0.0.0.255 172.20.200.0 0.0.0.255
access-list 150 permit ip 172.20.199.0 0.0.0.255 any
Checkpoint
IP address: 1.1.1.2
Network behind: 172.20.200.0/24
Create a network object that is the network that will be sitting behind the new Cisco router

Set the NAT – for Internet routing

Create a network object that is the network that will be sitting behind Checkpoint firewall:

Set the NAT – for Internet routing

Create a new interoperable device on CheckPoint for Cisco router

On Topology option, add external Interface

Note picture above is wrong (should be 1.1.1.1) – sorry$
Mark it as an external interface

Create an internal Interface:

Mark it as an Internal interface which leads to the network behind Cisco router

On the VPN domain option, choose manually defined: and assign the network that is behind Cisco router

On the VPN Manager, create a new community or join the new interoperable device to the existing community (either meshed or star)
Create a new one:

On the participating gateway, put the Cisco router and Checkpoint firewall

On the VPN properties, make sure the phase 1 and phase 2 is having the same setup in both Cisco (later) and Checkpoint
In this example we are using 3des-md5 for phase 1 and aes-128-md5 for phase 2

On the Advanced Properties, make sure the phase 1 and phase 2 is having the same setup in both Cisco (later) and Checkpoint
In this example we are using group 2 for phase 1 diffie-hellman group
Disable NAT inside VPN community – so that site-to-site VPN is not Natted

On Shared Secret page, put the share secret on to be used with Cisco router:

Create a rule in Checkpoint firewall to encrypt the traffic between network behind each firewall:

Push the policy to the CheckPoint firewall!
Cisco
IP address: 1.1.1.1
Network behind: 172.20.199.0/24
Create the isamkmp policy:
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
Create the crypto key:
crypto isakmp key
where shared-key is the shared key you setup in Checkpoint and 1.1.1.2 is the checkpoint IP address
Create transform set:
crypto ipsec transform-set cm-transformset-1 esp-aes esp-md5-hmac
Create the crypto-map:
crypto map cm-cryptomap 1 ipsec-isakmp
description VPN tunnel to Checkpoint
set peer 1.1.1.2
set security-association lifetime seconds 28800
set transform-set cm-transformset-1
match address 111
Create the outbound access list inside VPN (allow Cisco network to Checkpoint network):
access-list 111 permit ip 172.20.199.0 0.0.0.255 172.20.200.0 0.0.7.255
Create the inbound access list for external interface:
access-list 101 permit icmp any any
access-list 101 permit ip 1.1.1.2 0.0.0.0 any
access-list 101 permit ip 172.20.200.0 0.0.0.255 any
access-list 101 deny ip any any log
Assign crypto-map to the external interface:
interface Serial0/0
bandwidth 2048
ip address 1.1.1.1 255.255.255.0
ip access-group 101 in
no ip proxy-arp
ip nat outside
ip route-cache flow
no cdp enable
crypto map cm-cryptomap
Configure internal interface:
interface FastEthernet0/0
description Cisco LAN
ip address 172.20.199.254 255.255.255.0
no ip proxy-arp
ip nat inside
ip route-cache flow
speed 100
full-duplex
ntp broadcast
no cdp enable
Create the NAT rule:
ip nat inside source route-map nonat interface Serial0/0 overload
route-map nonat permit 10
match ip address 150
Create access list for NAT:
Do-not NAT traffic between sites
NAT everything else
access-list 150 deny ip 172.20.199.0 0.0.0.255 172.20.200.0 0.0.0.255
access-list 150 permit ip 172.20.199.0 0.0.0.255 any
No comments:
Post a Comment